Hackers are already flooding browsers with malware and phishing hyperlinks, and now researchers have found a vulnerability that offers them direct entry to providers in your laptop computer.
This vulnerability, often called 0.0.0.0 Day, impacts all Chromium-based browsers, together with Google Chrome, Firefox, Safari and Edge.
What’s regarding is that this vulnerability has been current in these browsers for the previous 18 years and has solely been found now.
SIGN UP FOR FOR KURT’S FREE NEWSLETTER AND GET INSTANT ACCESS TO THE CYBERGUY REPORT

An individual utilizing a laptop computer with Google Chrome browser (Kurt “CyberGuy” Knutsson)
What that you must know
The 0.0.0.0 Day vulnerability was found by the Israeli app safety agency Oligo and subsequently reported by The Hacker News. It entails the usage of IP handle, 0.0.0.0, which is generally innocent. But with this vulnerability, attackers may misuse it to entry and management native providers in your pc.
The important vulnerability “exposes a fundamental flaw in how browsers handle network requests, potentially granting malicious actors access to sensitive services running on local devices,” Oligo Security researcher Avi Lumelsky stated.
Security researchers have discovered that web sites with “.com” domains can talk with providers on a neighborhood community and run unauthorized code utilizing the handle 0.0.0.0. This vulnerability additionally permits them to bypass Private Network Access (PNA), which is meant to cease public web sites from accessing personal community endpoints instantly.
In easy phrases, this vulnerability may enable unhealthy actors to interrupt into your native providers and execute unauthorized actions in your machine.
The vulnerability impacts browsers together with Google Chrome, Edge, Safari and Firefox on units operating macOS and Linux. If you are a Windows person, you don’t have to fret as a result of Microsoft blocks this IP handle on the working system degree.

A browser displayed on a laptop computer (Kurt “CyberGuy” Knutsson)
HERE’S WHAT RUTHLESS HACKERS STOLE FROM 110 MILLION AT&T CUSTOMERS
Is a repair coming?
Chrome began blocking entry to the IP handle 0.0.0.0 from Chromium 128 in July. Google will steadily roll out this alteration, finishing it by Chrome 133, when the IP handle will probably be absolutely blocked for all Chrome and Chromium customers.
Meanwhile, Apple has already up to date WebKit, the browser engine utilized by Safari, to dam entry to 0.0.0.0. Mozilla has additionally blocked this IP handle in Firefox. To shield your self from getting affected, hold your browser updated.
HOW TO REMOVE YOUR PRIVATE DATA FROM THE INTERNET
Steps to replace your browser
The greatest solution to shield your self from safety flaws is to maintain your browser updated. Below are the steps to maintain it up to date.
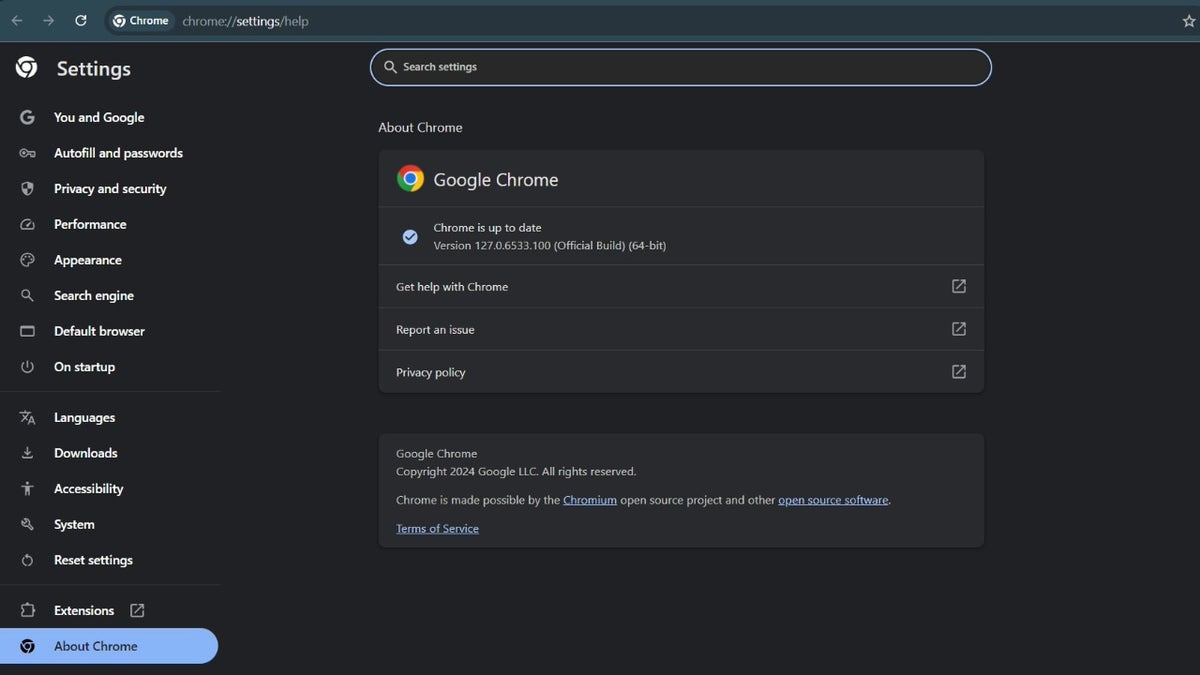
How to replace Chrome
- Open Google Chrome in your pc
- Click on the three dots within the top-right nook
- Select Help
- Click About Chrome
- Chrome will mechanically verify for updates. If an replace is on the market, it’ll obtain and set up it.
- Click Relaunch to finish the replace course of.
For cell units, you may replace Chrome by way of the Google Play Store (Android) or App Store (iOS) by looking for Chrome and tapping Update if out there
Google Chrome browser (Kurt “CyberGuy” Knutsson)
WORLD’S LARGEST STOLEN PASSWORD DATABASE UPLOADED TO CRIMINAL FORUM
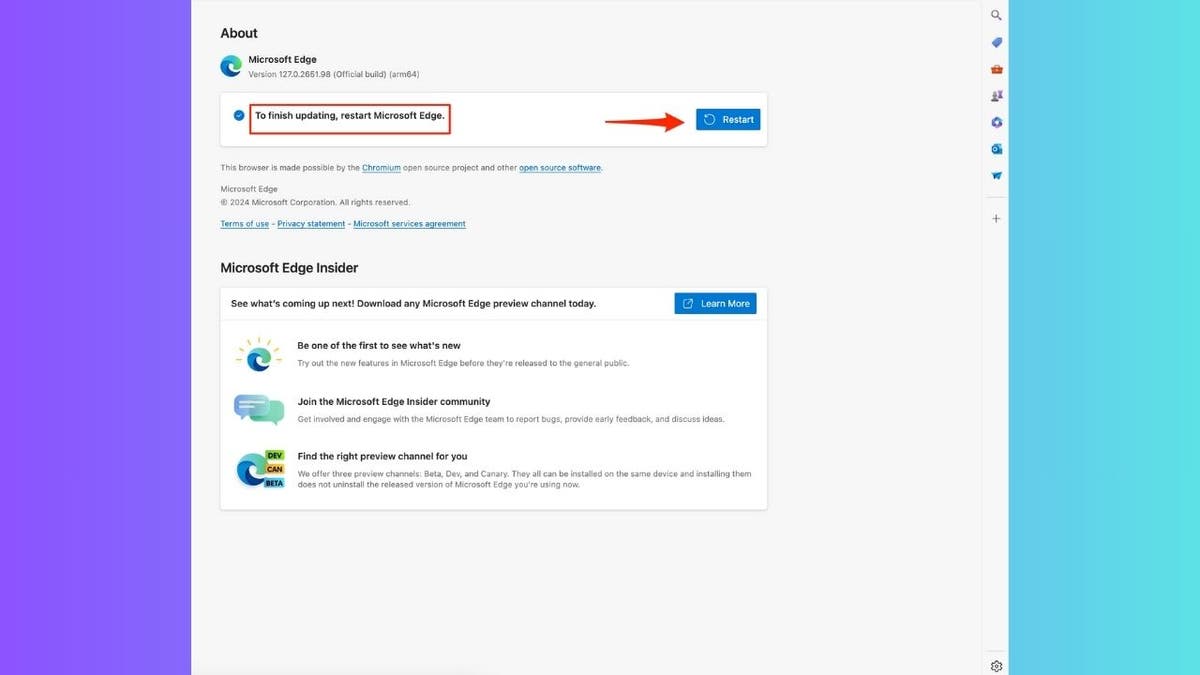
How to replace Microsoft Edge
- Open Microsoft Edge
- Click on the three dots within the top-right nook
- Select Help and suggestions
- Click About Microsoft Edge
- Edge will mechanically verify for updates and set up them if out there
- Click Restart to replace Microsoft Edge and apply any updates
For cell units, updates could be achieved by the respective app shops (Google Play Store for Android and App Store for iOS) by looking for Edge and tapping Update if out there.
Microsoft Edge browser (Kurt “CyberGuy” Knutsson)
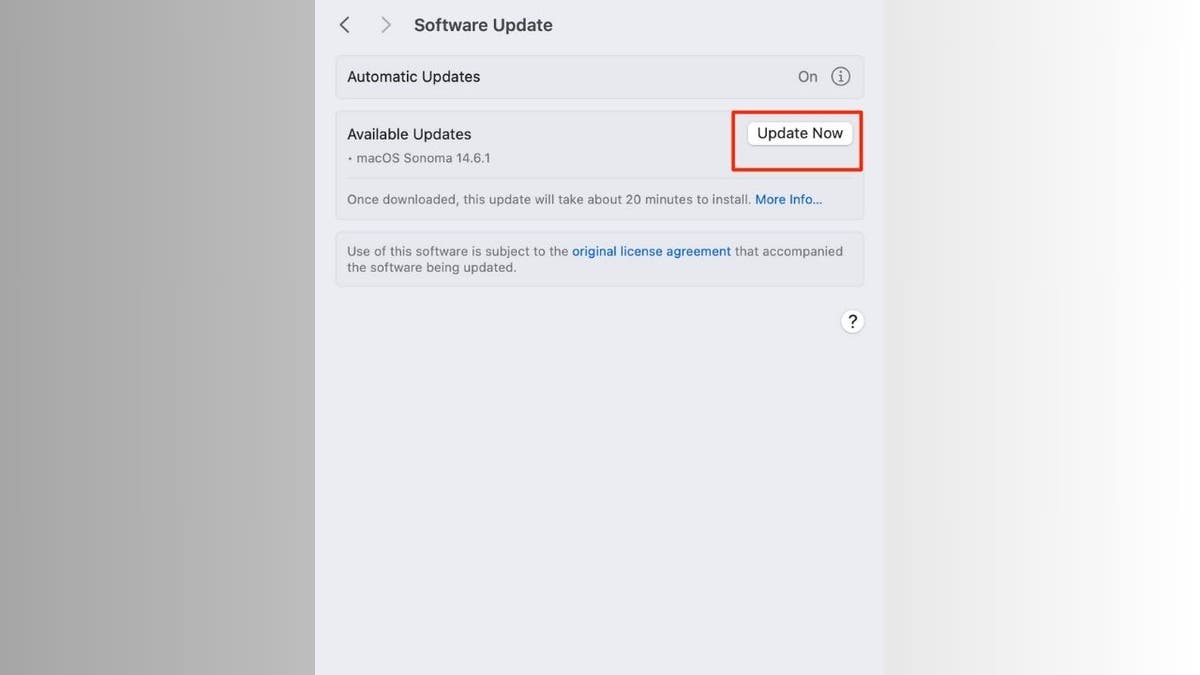
How to replace Safari
- On a Mac, open the Apple menu
- Select System Settings
- Tap General
- Click Software Update
- If an replace for Safari is on the market, click on Update Now.
- Follow the prompts to finish the set up.
For iOS units, updates are achieved by the Settings app beneath General > Software Update.
Safari browser (Kurt “CyberGuy” Knutsson)
How to replace Mozilla Firefox
- Open Firefox
- Click on the three horizontal traces (☰) within the top-right nook
- Select Help
- Click About Firefox
- Firefox will verify for updates and obtain them mechanically
- Click Restart to Update Firefox if an replace was put in
For cell units, you may replace Firefox by the Google Play Store (Android) or App Store (iOS) by looking for Firefox and tapping Update if out there.
CLICK HERE FOR MORE U.S. NEWS

Mozilla Firebox browser (Kurt “CyberGuy” Knutsson)
GET FRESH BUSINESS ON THE GO BY CLICKING HERE
Additional measures to maintain your knowledge and units secure
Below are some additional steps to take to stop being affected by hackers exploiting safety vulnerabilities.
1. Have sturdy antivirus software program: Hackers usually acquire entry to units by sending contaminated emails or paperwork or tricking you into clicking a hyperlink that downloads malware. You can keep away from all of this by putting in sturdy antivirus software program that may detect any potential menace earlier than it may well take over your machine or router.
The greatest solution to safeguard your self from malicious hyperlinks that set up malware, doubtlessly accessing your personal data, is to have sturdy antivirus software program put in on all of your units. This safety can even provide you with a warning to phishing emails and ransomware scams, holding your private data and digital belongings secure. Get my picks for the most effective 2024 antivirus safety winners in your Windows, Mac, Android and iOS units.
2. Recognize pressing requests as potential scams: Always be cautious if somebody is urgently requesting you to do one thing like ship cash, present private data or click on on a lin. Chances are it’s a rip-off.
3. Use sturdy and distinctive passwords: Create sturdy passwords in your accounts and units and keep away from utilizing the identical password for a number of on-line accounts. Consider utilizing a password supervisor to securely retailer and generate advanced passwords. It will allow you to to create distinctive and difficult-to-crack passwords {that a} hacker may by no means guess. Second, it additionally retains observe of all of your passwords in a single place and fills passwords in for you if you’re logging into an account so that you simply by no means have to recollect them your self. The fewer passwords you keep in mind, the much less possible you may be to reuse them in your accounts. Get extra particulars about my greatest expert-reviewed Password Managers of 2024 right here.
4. Enable two-factor authentication: Enable two-factor authentication at any time when doable. This provides an additional layer of safety by requiring a second type of verification, similar to a code despatched to your cellphone, along with your password.
ANDROID USERS AT RISK AS BANKING TROJAN TARGETS MORE APPS
Kurt’s key takeaway
Given the newly found 0.0.0.0 Day vulnerability, it is extra necessary than ever to maintain your browser updated. While main browser corporations are actively engaged on a repair, staying on high of software program updates is essential to guard your machine. To additional safeguard your on-line expertise, be cautious of suspicious hyperlinks, apply secure searching habits, and recurrently verify for updates.
CLICK HERE TO GET THE FRESH NEWS APP
Given the current discovery of the 0.0.0.0 Day vulnerability affecting main browsers like Google Chrome, Firefox, Safari and Edge, which has been current for 18 years, do you assume tech corporations are doing sufficient to make sure the safety of their merchandise and shield customers from such long-standing vulnerabilities? Let us know by writing us at Cyberguy.com/Contact
For extra of my tech ideas and safety alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter
Ask Kurt a query or tell us what tales you would like us to cowl
Follow Kurt on his social channels
Answers to probably the most requested CyberGuy questions:
Copyright 2024 CyberGuy.com. All rights reserved.


